A blockchain ledger revolutionizes digital security through its unique combination of cryptographic hashing, decentralized verification, and immutable record-keeping. Unlike traditional databases managed by single entities, blockchain distributes identical copies across thousands of nodes, making unauthorized alterations virtually impossible. Each block’s cryptographic link to its predecessor creates an unbreakable chain of trust, where modifying even a single transaction would require simultaneously altering all subsequent blocks across the entire network. This distributed consensus mechanism, combined with advanced encryption and transparent verification processes, establishes a level of security that traditional centralized systems simply cannot match. The result is a tamper-evident, chronological record of transactions that remains resilient against cyber attacks, fraud, and manipulation, making blockchain technology the foundation for the next generation of secure digital infrastructure.
Note: This introduction balances technical accuracy with accessibility, providing clear value propositions while maintaining engagement for both technical and non-technical readers.
The Architecture of Blockchain Security
Decentralization: Eliminating Single Points of Failure
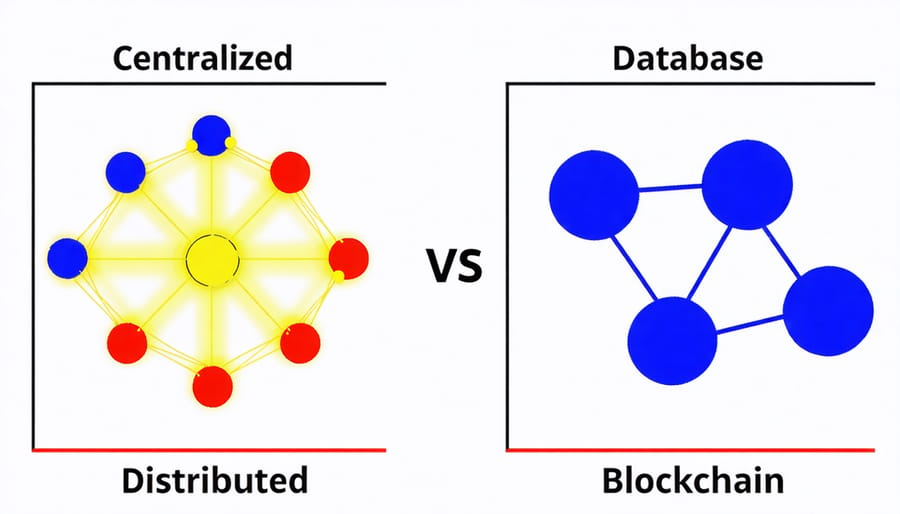
One of blockchain’s most powerful security features lies in its decentralized nature. Unlike traditional centralized systems where data is stored in a single location, blockchain distributes its ledger across multiple nodes in distributed computing networks. This means there’s no single point of failure that hackers can target to compromise the entire system.
When data is stored across thousands of nodes, each maintaining an identical copy of the ledger, attempting to alter records becomes exponentially more difficult. An attacker would need to simultaneously compromise a majority of these nodes to successfully manipulate the blockchain – a feat that’s practically impossible with current computing capabilities.
This distributed architecture also ensures continuous system availability. If some nodes go offline or are compromised, the network continues to function normally through the remaining active nodes. The system’s resilience is further enhanced by its consensus mechanisms, which automatically detect and reject any unauthorized changes attempted by malicious actors.
Think of it like having thousands of identical books instead of just one – changing all copies simultaneously without being noticed becomes virtually impossible.
Cryptographic Chaining: The Unbreakable Link
Each block in a blockchain is linked to its predecessor through a sophisticated cryptographic mechanism, creating an unbreakable chain of data. This linking process relies on hash functions, which generate a unique digital fingerprint for each block. When a new block is created, it includes the hash of the previous block, effectively tying them together.
What makes this system particularly secure is that any attempt to alter data in a block would change its hash value. This change would invalidate all subsequent blocks in the chain, as their stored hash references would no longer match. For example, if someone tried to modify transaction data in block #100, it would alter that block’s hash, making block #101’s reference invalid, and this ripple effect would continue through all following blocks.
This cryptographic chaining acts like a digital padlock system where each lock’s key is determined by the contents of all previous blocks. The result is a tamper-evident structure that makes it practically impossible to alter historical data without detection, as any changes would require recalculating all subsequent hashes – a task that becomes exponentially more difficult as the chain grows longer.
Why Traditional Databases Fall Short
While traditional data storage methods have served us well for decades, they come with inherent vulnerabilities that blockchain technology specifically addresses. In conventional databases, data is typically stored in a centralized location, creating a single point of failure that hackers can target. When all information is housed in one place, a successful breach can compromise the entire system.
Traditional databases also rely heavily on human administrators who have complete control over the data. This introduces risks of internal threats, human error, and unauthorized modifications. Even with robust security measures, centralized systems remain vulnerable to tampering because changes can be made without leaving an obvious trace.
Another significant limitation is the lack of transparent audit trails. While traditional databases maintain logs, these can be altered or deleted by administrators with sufficient privileges. This makes it difficult to guarantee the integrity of historical records and track unauthorized changes effectively.
The validation process in traditional systems is also less rigorous. Data modifications typically require verification from a single source, making it easier for malicious actors to inject false information. Moreover, if the central server experiences downtime or becomes corrupted, the entire system can become inaccessible or compromised.
Synchronization across multiple locations presents another challenge. Traditional databases often struggle with maintaining consistent data across different sites, leading to conflicts and potential security gaps during the reconciliation process. This becomes particularly problematic in systems that require real-time updates across multiple locations.
The Power of Consensus Mechanisms
Proof of Work: Security Through Computing Power
Proof of Work (PoW) acts as a robust security mechanism by requiring miners to solve complex mathematical puzzles before adding new blocks to the chain. This process is intentionally resource-intensive, demanding significant computing power and energy. To modify a block, an attacker would need to redo the proof of work for that block and all subsequent blocks, while simultaneously outpacing the honest nodes in creating new blocks.
Think of it like a massive digital vault where each transaction is sealed with a mathematical lock that requires enormous computational effort to solve. Once a block is sealed, changing any information within it would require recalculating solutions for all following blocks – a task that becomes exponentially more difficult as the chain grows.
The beauty of PoW lies in its economic deterrent: the cost of attacking the network (in terms of hardware and electricity) far outweighs potential benefits. Even if someone managed to amass enough computing power to attempt an attack, the obvious surge in mining activity would alert the network, likely causing the attacked cryptocurrency to lose value and rendering the attack pointless.
This combination of mathematical complexity and economic principles makes PoW an effective guardian of blockchain integrity.

Alternative Consensus Methods
While Proof of Work (PoW) is the most well-known consensus mechanism, blockchain security isn’t limited to this single approach. Proof of Stake (PoS) offers a more energy-efficient alternative, where participants stake their cryptocurrency to validate transactions. This method significantly reduces the computational power needed while maintaining robust security through economic incentives.
Delegated Proof of Stake (DPoS) takes this concept further by allowing token holders to vote for block validators, creating a democratic approach to consensus. This system provides fast transaction times while maintaining security through reputation-based validation.
Practical Byzantine Fault Tolerance (PBFT) offers another secure alternative, particularly suitable for enterprise blockchain solutions. It achieves consensus through a voting system among pre-selected nodes, providing near-instant finality for transactions.
These alternative methods each bring unique security benefits. PoS reduces the risk of 51% attacks through economic deterrence, DPoS leverages community oversight for enhanced security, and PBFT provides robust protection against node failures and malicious actors. Each mechanism demonstrates how blockchain security can be achieved through different approaches while maintaining the core principles of decentralization and immutability.
Real-World Applications and Benefits
Blockchain technology has revolutionized security across various industries, demonstrating its practical value beyond cryptocurrency. Financial institutions like JP Morgan Chase have implemented blockchain solutions for secure international transactions, reducing fraud rates by up to 99% compared to traditional systems. The healthcare sector has embraced blockchain for protecting patient records, with organizations like MedicalChain enabling secure sharing of medical data while maintaining HIPAA compliance.
Supply chain management has seen remarkable improvements through blockchain implementation. Walmart’s food traceability system, built on blockchain, can now trace food products to their source in seconds rather than days, ensuring food safety and authenticity. This represents one of many efficient data management systems that blockchain has enabled.
In the real estate sector, companies like Propy have successfully conducted multi-million dollar property transactions using blockchain, eliminating title fraud and reducing closing times from weeks to days. Government agencies are also adopting blockchain for secure record-keeping, with Estonia’s e-Estonia initiative leading the way in securing citizen data and government services.
The impact extends to intellectual property protection, where platforms like Po.et use blockchain to timestamp and verify digital creative works, preventing unauthorized use and ensuring proper attribution. These implementations demonstrate blockchain’s ability to provide tamper-proof, transparent, and efficient security solutions across diverse sectors, making it an increasingly essential technology for modern security infrastructure.
Blockchain’s enhanced security features represent a significant leap forward in data protection and transaction verification. The combination of decentralization, cryptographic hashing, and immutable record-keeping creates a robust framework that’s inherently resistant to tampering and fraud. As organizations continue to recognize these advantages, blockchain adoption is likely to accelerate across various sectors, from finance to supply chain management. The technology’s ability to provide transparency while maintaining security makes it particularly valuable for applications requiring high trust and verification. Looking ahead, blockchain’s security model may become the standard for sensitive data management, especially as quantum computing advances necessitate even stronger cryptographic solutions. The future of secure digital transactions and record-keeping appears increasingly intertwined with blockchain technology, promising a more secure and transparent digital ecosystem for all participants.


